Are you a trader, analyst, or data enthusiast looking for reliable historical stock market data for India? Look no further!
I am offering a comprehensive dataset covering Indian stock data from 2015 to August 2025. This dataset is perfect for backtesting trading strategies, algorithmic trading, research, or learning the Indian stock market trends.
What’s included:
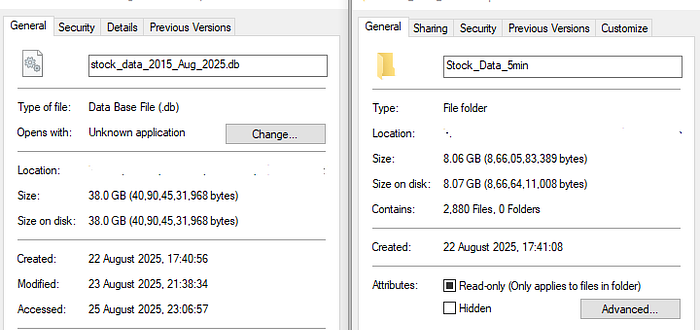
Stock Database (.db) — stock_database_.db_File_2015_Aug_2025_5min.rar
SQL database format
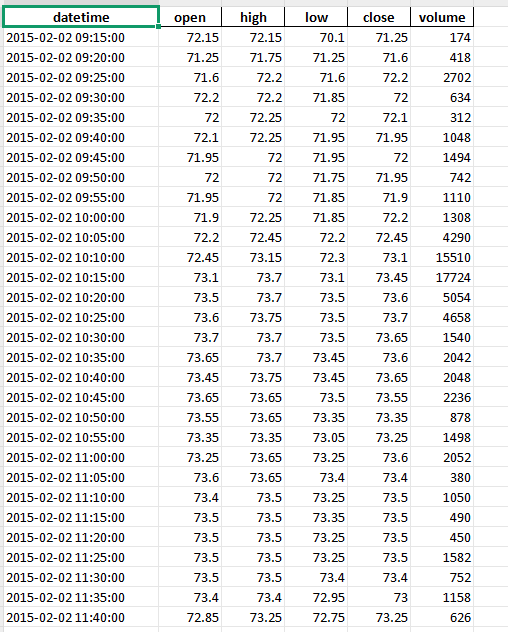
Contains 5-minute interval data for all major Indian stocks
Easily queryable for automated backtesting or analysis
Stock Data in Excel (.xlsx) — Stock_Data_Excel_5min.rar
Excel spreadsheets for easy access
Ideal for manual analysis or visualization
Includes OHLCV data (Open, High, Low, Close, Volume)
Why this dataset is valuable:
10+ years of high-resolution historical data — perfect for analyzing long-term trends
Ready-to-use formats — database for coders, Excel for analysts
Affordable price — get all this for just ₹1000
Whether you are a professional trader, a student learning stock markets, or an AI developer building trading algorithms, this dataset will save you countless hours of data collection and cleaning.
How to purchase:
Message me on Telegram “@Lazyhacker22”
Pay ₹1000 via UPI / QR code / preferred method.
Get instant download access to both .db and Excel files.
Download:
Stock Data in Excel (.xlsx) — Stock_Data_Excel_5min.rar
https://drive.google.com/file/d/1XZIKoJ3CjjCLtyvQ-aU19UJCoS6ewErr/view?usp=sharing
Stock Database (.db) — stock_database_.db_File_2015_Aug_2025_5min.rar
https://drive.google.com/file/d/1BVOEEYEKyS7mVg-VqbqZCQ9jThyFrAWM/view?usp=sharing
Don’t miss out on the chance to own a ready-to-use, 10-year Indian stock market dataset that can accelerate your trading strategies and research.
Invest in knowledge today — download your dataset now!



Comments
Post a Comment