Is your webcam exposed on the internet and everyone enjoying your personal moments? | How to check webcam or security camera is exposed on the internet or not?
Nowadays we start using many technology devices in our homes. Many people are installing CCTV or security cameras in their houses, private rooms, offices, private places, etc for security purposes and monitoring, but many of them don't know how to configure that device securely.
So let's talk about CCTV and security cameras only.
What do most CCTV/Security camera users believe?
Most users believe that using a strong username and password on a camera administrative page protects them. (Partially true in the case of online cameras)
Example:
Why it is partially true?
It's partially true because you are protecting only the camera administrative page which is also an important part. Still, you are not protecting the protocol used to control streaming media servers (Real-Time Streaming Protocol (RTSP)).
I have seen many online webcams whose administrative page is secured by strong credentials, but they forget to secure the RTSP protocol which gives me access to the streaming video. Indirectly, I was able to see the streaming video without actually need for credentials. In most of the scenarios the RTSP protocol has no credentials or weak credentials are configured.
Let's take a real-life example of the same
and
How to find whether our webcam is exposed on the internet or not:
- Assume that my public IP address is 68.174.46.58.
- You can check your public IP address on https://ipinfo.me/ or https://www.whatismyip.com/
- Now do a port scan on the public IP address, I know many of you are not from a technical background, just follow the steps that I have mentioned.
- Download the port scanner from https://nmap.org/download and install it in your system. If you are using Linux you can install it by using sudo apt-get install nmap.
- After installing the Nmap, open it and put the public IP address in "Target" if you open Zenmap GUI, otherwise use cmd/terminal for running the command.
CMD/Terminal Command:
nmap -Pn <public IP address> -sV --open
- If you see the above images, you will find 554 (RTSP) that port you need to check if it's publically exposed or not. In the same way, you can check for all ports and services exposed by the device over the internet. Like here in this scenario ports 81 and 82 is looks interested.
- To check the RTSP, you need a VLC player. Download from here: https://www.videolan.org/vlc/ and install it.
- After installation opens it. Click on "Media" then click on "Open Network Stream" then click on "Network" and in "Please enter the network URL:" type this rtsp://<your public IP address>:<rtsp port>/ and in the last click on "Play". Wait for some minutes (2-3 minutes) because sometimes it takes some minutes while searching the streaming path over the internet.
- Till now, we identify that my webcam is exposed on the internet and anybody can see the webcam streaming. Now time to check the administrative page whether it's exposed on the internet or not if yes, is it protected by a strong password or not.
- Now open your browser and try to access HTTP or HTTPS ports like in my case I have a doubt on ports 81 and 82 and I know here HTTP is not mentioned but because of my experience I know it's HTTP protocol.
- When I entered http://68.174.46.58:81/ and http://68.174.46.58:82/ in my browser, it opens a webcam administrative page and asked for credentials.
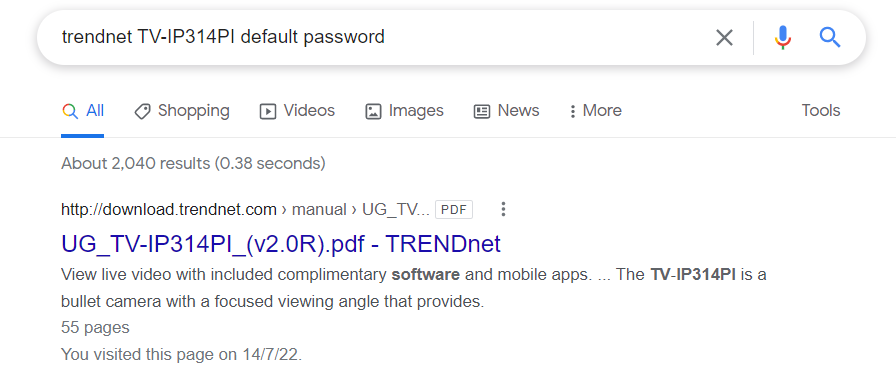
- I searched for a default credential for this webcam by typing "trendnet TV-IP314PI default password" in Google and I found a PDF file for the same version. I downloaded it and search for default credentials.
- I tried that credential but it was not working. So it's confirmed that I am not using default credentials.
The strong password guideline:
The password should be minimum 8 characters long.
The password should contain special characters, alpha-numeric and upper-lower case characters. Example (LolZ@13e7!*()Xco)
- Always use a strong username and strong password in the CCTV camera administrative login page.
- Check for the RTSP authentication option in the CCTV camera before buying a CCTV camera.
- Ask the vendor to enable RTSP authentication and strong credentials while installing the camera.
- Try not to install the CCTV camera in your bedroom :P (I don’t know why people are installing it in their bedroom and also providing internet access)
- If not needed, don’t give internet access to the CCTV camera and its administrative login page
- Check on Google or ask your vendor “how to enable authentication for rtsp”
- Default RTSP protocol is 554, change this port to a random port.
- Update your CCTV camera firmware whenever it’s available.
Lack of technical awareness leads to being vulnerable.









Comments
Post a Comment