What is NMAP?
NMAP-Network mapper as the word suggests is a tool used to scan networks for open, closed, filtered ports, services running on a system, OS detection, or guessing!, finding some vulnerabilities.
It is written by Gordon Lyon.
As per my experience, it is the best handy tool, and easy to use for network scanning.
In this tutorial, I’ll cover some of the Kung-Fu basics of NMAP with examples.
Let’s say you want to scan a host to see what the version of services running. To do this, run the following command:
nmap -sV target
Here TypeOptionTarget meaning is -sV which stands for scanning and V stands for version.
How NMAP works as a default:
When you run default command ("nmap x.x.x.x/xx). First NMAP starts doing HOST discovery, then Domain discovery, and then Port scanning.
Now let’s start playing with different scenarios where NMAP is mostly used at the time of Pentesting:
-sS: TCP SYN SCAN
This technique is the best technique I found for scanning a network as this is stealth scanning or we can say half-open scanning.
Half-open means this scan never makes any full TCP connection to check open-closed, or filtered ports by this option, no scanning logs create on the victim side. An attacker sends an SYN packet to the victim if the port is open then the victim sends an ACK response to the attacker which means the port is open and the attacker sends RST to the victim so that a full TCP connection is not established it’s only done when you are login as a root user because this signal sends at kernel level otherwise victim send RST if the port is closed but sometimes no response come from victim side that means ports are filtered or we can say some firewall mechanism there. ports are marked as a filter also when ICMP unreachable error (type 3, code 0, 1, 2, 3, 9, 10, or 13) is received that's why we used -Pn option also that I will explain in the next scenario.
Advantages of the TCP SYN Scan
The TCP SYN scan never actually creates a TCP session, so isn't logged by the destination host's applications. This is a much "quieter" scan than the TCP connect() scan, and there's less visibility in the destination system's application logs since no sessions are ever initiated. Since an application session is never opened, the SYN scan is also less stressful to the application service.
Disadvantages of the TCP SYN Scan
The TCP SYN scan requires that NMAP have privileged access to the system. Without privileged access, NMAP can't create the raw packets necessary for this half-open connection process.
When to use the TCP SYN Scan
The SYN scan is a common scan when looking for open ports on a remote device, and its simple SYN methodology works on all operating systems. Because it only half-opens the TCP connections, it's considered a very 'clean' scan type.
-sU: UDP SCAN
UDP scan is the most time taking scan I found, but important also as most security testers ignore this scan. Ports like DNS(53), SMTP(161/162), and DHCP(67/68) are the most common UDP ports in which high vulnerability is found, vulnerability like DNS Zone Transfer.
Advantages of the UDP Scan
Since there's no overhead of a TCP handshake, the UDP scan is inherently less "chatty" once it finds an open port. However, if ICMP is responding to each unavailable port, the number of total frames can exceed a TCP scan by about 30%!
Microsoft-based operating systems do not usually implement any type of ICMP rate limiting, so this scan operates very efficiently on Windows-based devices.
Disadvantages of the UDP Scan
The UDP scan only provides port information only. If additional version information is needed, the scan must be supplemented with a version detection scan (-sV) or the operating system fingerprinting option (-O).
The UDP scan requires privileged access, so this scan option is only available on systems with the appropriate user permissions.
When to use the UDP Scan
Because of the huge amount of TCP traffic on most networks, the usefulness of the UDP scan is often incorrectly discounted. There are numerous examples of open UDP ports caused by spyware applications, Trojan horses, and other malicious software. The UDP scan will locate these open ports and provide the security manager with valuable information that can be used to identify and contain these infestations.
-sA: TCP ACK SCAN
This type of scan is used to detect the firewall ruleset whether it is a stateful firewall or not and which ports are filtered. With this option, we are able to scan filtered or unfiltered ports. It doesn’t scan open or closed ports.
Stateless firewalls restrict or block packets based on source and destination or some static values. A stateful firewall can watch traffic stream from end to end. This means that stateful firewalls can tell what stage a TCP connection is in (open, open sent, synchronized, synchronization acknowledge or established), it can tell if the MTU has changed, whether packets have fragmented, etc.
When using this option NMAP send a packet where only the ACK flag is set, when scanning the unfiltered system open and closed port will both return the RST packet it’s mean that the ports are unfiltered, If doesn't get any response or get ICMP error message that means ports are filtered.
Advantages of the ACK Scan
Since the ACK scan doesn't open any application sessions, the conversation between Nmap and the remote device is relatively simple. This scan of a single port is unobtrusive and almost invisible when combined with the other network traffic.
Disadvantages of the ACK Scan
The ACK scan's simplicity is also its largest disadvantage. Because it never tries to connect to a remote device, it can never definitively identify an open port.
When to use the ACK Scan
Although the ACK scan doesn't identify open ports, it does a masterful job of identifying ports that are filtered through a firewall. This list of filtered and unfiltered port numbers is useful as reconnaissance for a more detailed scan that focuses on specific port numbers.
-sV: Version Detection
This option is the best option for hackers as we directly find the version so it’s easy for us to detect exploits related to the version. You can use more options with this option like –allports by default NMAP skip TCP port 9100 because some printers simply print anything sent to that port. Another option is –version-intensity <intensity_number> between 1-9 by default NMAP scan with intensity_number value 7 more the number more likely it is the service correctly identified.
Advantages of Using Version Detection
Version information is valuable information! Version scanning for service information provides easier management of patches and updates. A network security manager can scan every host in an organization to verify that the software is in the correct version. Stations showing older software revisions are identified and further action can be taken.
The version information scan can also assist in locating software that is not compliant with organizational standards. This is also an easy method of verifying the licenses of application services. Nmap can find all of the devices running a specific version of server software to determine if the quantity meets the organization's licensing agreements.
Disadvantages of Using Version Detection
The version scan is very invasive because of the probing that must occur to prompt the service for information. The fingerprint comparison must have information from the application to compare to the fingerprint in the nmap-service-probes file, and this process transmits a number of packets between the source and destination.
The version scan also opens sessions with the remote applications, which will often display in an application's log file. These sessions are almost always necessary, and can't be avoided if the version scan is going to decisively determine the application type and version.
Version detection will only work with TCP or UDP port scans. The ping scan (-sP), the list scan (-sL), and the IP protocol scan (-sO) will not run on the same command line with version detection.
When to use Version Detection
The name and version of the service can provide the security team with information that it can use to keep the network applications patched and up-to-date. The server team can use version scans to confirm that a series of upgrades have been completed successfully. If unknown stations are found during a ping scan, the version scan can help determine what applications these 'rogue' stations are providing!
-Pn: No Ping
By default, NMAP first does host discovery by pinging that IP address if gets no ping response then NMAP considered it down and stops further scanning but most of the time there is a firewall or ICMP packet block, So this option used NMAP takes the target IP address as up and start requested scanning function on target IP.
In the below POC host is down but when using -Pn option it always considers it as up, here I am using –disable-arp-ping because the IP is in the same LAN, and in the same LAN arp scanning is first performed.
-p: Port Range
This option is mostly used to scan a specific port number, most of the time we only need details about, a specific port number only so scanning all ports is all time waste. You can use -p <port number> example -p 80,53,21 like this but point to be noted that most of the time we found ports that are UDP but also in TCP or vise-versa so in that case you have to mention option like -p T:21-25,808080 for TCP and -p U:53,111,123 for UDP. You can use -p- an argument also to scan all ports from 1-65535.
Most of the time SMTP works on different ports also other than 25 so to scan SMTP service you can scan by name -p smtp or if you want to scan all ports whose name begins with HTTP then you can use this argument -p http* .
-O: OS Detection
This option helps you to find OS, and OS helps to find exploits according to the OS version used. For example, by opening ports we get that Window is running on the victim system but if we get window version let's say if we get that victim system using window XP then it’s easy for us to find exploit according to that version and chances also increase for the exploitation.
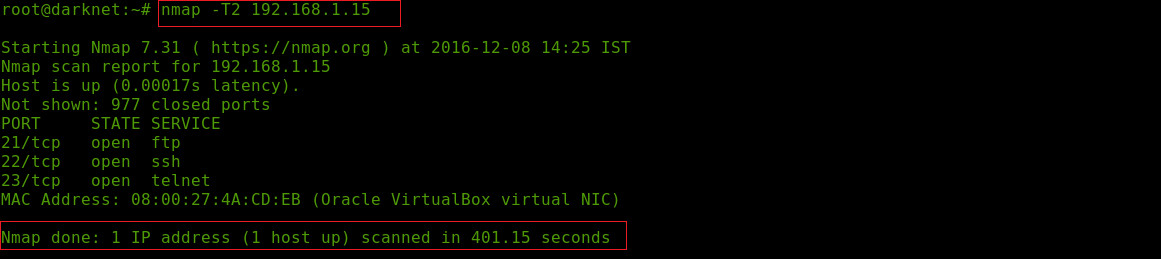
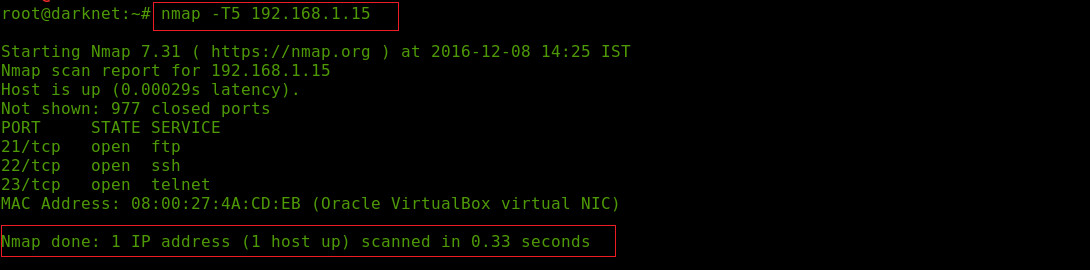
-T:<0-5> Timing Templates
This option is used for increasing or decreasing the speed of the scan according to your need and as per your network speed. Argument -T0 and -T1 may be used for avoiding IDS alert that's why it takes more time to scan the ports as it takes less bandwidth and targets machine resources, -T2 is a polite scan,-T3 it’s a default NMAP scan option,-T4 is aggressive scan and -T5 is insane scan this scan option used to scan target ip fast but this options less come in work if target side has firewall or IDS or something like that and this option only used when you have good bandwidth speed.
-f: Fragment packets
This technique was widely used in old days in this technique when we used the -f option NMAP can fragment packets in 8 bytes when we doing this scan type. Nowadays it’s also used when the firewall is not properly configured so it can bypass the packet inspection of firewalls.
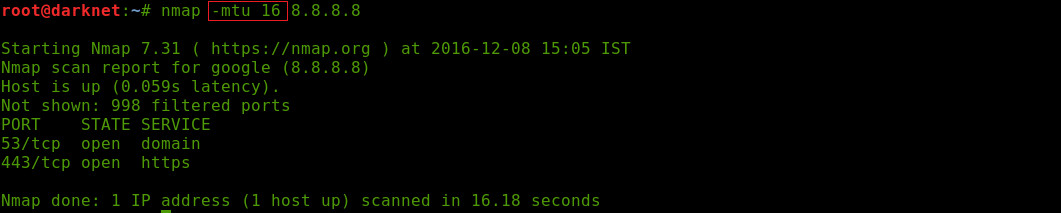
-mtu <number>: Maximum Transmission Unit
This is the same technique as above mentioned, the only difference is that here you can give your own MTU. Example nmap -mtu 24 victim_IP.MTU is always in the multiple of 8 like 8,16,24,32...
-D: Decoy Address
Most of the time IDS or firewalls detect scans by logs so for avoiding this you can use the -D option with spoof Ips and your IP, like this -D <spoofed ip1>,<spoofed ip2>,.....,<your ip>,<spoofed ip8>. In firewall logs, it will be not only our IP address but also the IP address of the decoys so it will be much harder to determine from which system the scan started.
--source-port
The most common error that many administrators are doing when configuring firewalls is to set up a rule to allow all incoming traffic that comes from a specific port number. The –source-port option is used to exploit this misconfiguration. Common ports that are mostly used for this type of scan 20,53 and 67.
When we do a normal scan:
When we do scan with --source-port option:
--data-length
Most firewall inspects packets by looking at their packet size in order to identify a port scan. This is because many scanners are sending packets that have specific sizes so to avoid detection you can use –data-length 25 or any other number to add additional data and send packets with a different size than the default.
When we do a normal scan:
When we do scan with --data-length option:
--spoof-mac
This technique is very effective especially if there are MAC filtering rules that allow only traffic from certain MAC addresses, So you will need to discover which MAC address you need to set in order to obtain results. This option also gives you the ability to choose a MAC address from a specific vendor, choose a random MAC address, or set a specific MAC address of your choice.
--spoof-mac Dell/Apple/Hp -> Specific MAC address from vendor
--spoof-mac 0 -> Generate a random MAC address
--spoof-mac 00:01:02:55:45:AE -> Specific MAC address
--proxies
This option helps you to hide the true source of the scan or evade certain firewall restrictions, but it can hamper scan performance by increasing latency. You only use HTTP and SOCKS4 proxies for scanning. This option is still under development and has limitations.
nmap --proxies http://x.x.x.x:port -sS victim_ip
-A: Aggressive Scan
This option help for doing OS detection (-O),Version scan(-sV),Script scanning(-sC) and traceroute (--traceroute) at once. The point is to enable a comprehensive set of scan options without people having to remember a large set of flags but as per my experience do scan manually. This option only enables features, and not timing options (such as -T4) or verbosity options (-v) that you might want as well.
These are the options which mainly used for scanning there are more other options that you can learn from the below references.
Conclusion:
The above-shown example is the basics of how attackers or pentesters use NMAP for scanning networks.
NMAP is a very powerful tool and it has the ability to cover the very first aspects of penetration testing, which include information gathering and enumeration. This article was written in an effort to discuss NMAP's mostly used options.
There are so many other things that you can do with the NMAP. You can learn this from NMAP books or below mentioned references.
Useful resources:
Following is the list of valuable resources from which you can get more information on NMAP in deep.
1. NMAP BOOK
4. DEFCON Video
Thank you for reading this post, feel free to comment and discuss.
"Network Scanning Is A Art For Gathering Useful Information"
Happy Scanning :)





























Comments
Post a Comment