I was also confused while understanding both concepts, I thought that the Gmail/Facebook credentials that I used to login into abc.com is an OAuth concept but I was wrong. It is the OpenID concept that is working on the OAuth protocol.
So What is OAuth?
OAuth = Open Authorization
As the name suggests it is “Authorization” which means it’s related to some authorization concept.
As the internet grows, the developer needs some concept so that “abc.com” can read the data from “anything.com” without giving the password of anything .com to the abc.com server. It helps in improving the user experience and also increases the business.
Let’s explain an OAuth by a simple example:
I am sure, we all have seen this type of concept, where we logged into an application (abc.com) by using abc.com credentials and after that, we get the option like import contacts from Gmail. When we click on that hyperlink, it redirects us to Gmail, where it asks for Gmail credentials, and after entering the credential, it asks for the approval that abc.com need permission to access your contact something like that and there you select “Yes”/”Approved”. After that, all email IDs in your Gmail start showing in the abc.com account.
So that’s called OAuth. So here in this scenario, the OAuth provider is Gmail.
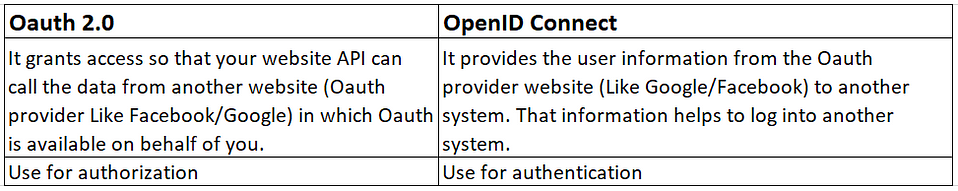
OAuth is an Open Authorization protocol that allows the third-party application or OAuth client to access the user data (like name, email, contacts, etc.) from the OAuth provider (Gmail, Facebook, etc.) without exposing the OAuth provider credential to the OAuth client/Third party application.
When we approve the request like in the above example, we approved the contact access by abc.com, we are telling the OAuth provider (Gmail) that abc.com is allowed to access my email on behalf of me and please provide the data that I have approved. It is called OAuth, it is used for authorization, not for authentication.
For authentication, we need a concept called OpenID connect which works on the OAuth protocol.
OAuth solved the biggest problem that many of the web services were struggling to find the solution. As OAuth was so popular that everyone started using it. So some developers started using the OAuth concept as the authentication. Now you are thinking about how it’s possible if it’s an authorization protocol and how it can be used for authentication.
The developer believes that if the user is able to log into their OAuth provider account (Gmail/Facebook) then it’s a legitimate user and for an authentication system what first thing do we actually need? In terms of information, you may want to know the user name or the email address of the user that just logged in at least. So by tweaking the OAuth protocol developers started using it for authentication.
So what’s the problem while using the OAuth as authentication?
The problem was that everybody was using their own way to use the OAuth protocol as authentication. There was no standard for using it. This makes a developer confused before OpenID connect. For authentication websites need data to know who you are? OpenID connect, solve this by making a standard way to use OAuth authentication or we can say OpenID connect is an extension of OAuth protocol.
In OAuth, we get an access token by using an authorization code, and in OpenID connect we get an access token and ID token by using an authorization code. The ID token is a JWT token that contains information about the user. In OpenID connect we can ask for extra information if needed, we can ask by using the scope parameter in the request.
OpenID Connect request has a scope OpenID parameter:
* Scope: OpenID
The ID token is used by the website to understand more about the user as its JWT token, it’s decrypted and read by the website. If the website needs more data about the user, it can use an access token to read more data about the user like user info.
This is just a basic idea about both OAuth and OpenID connect. Hope it helps you.
Reference:
https://www.youtube.com/watch?v=996OiexHze0&t=44s
#OAuth #OpenID #OpenIDConnect
Comments
Post a Comment