OkCupid LIKE Restriction Bypass
Somebody said, “Loneliness help you to think differently”. I was abroad for a project and was feeling very bored there as this was my fourth time here at the same place. I was checking my Instagram and I saw an advertisement for “OKCupid” “Dating Deserves Better”. I thought this was a good way for time to pass and to know new humans. I installed the application and started “Right Swipe” as a normal male human.

After some “Right Swipe” the application started asking for money and blocked my “swipe” for 10 hours. Now again I started feeling bored and the question came in my mind. How this application blocked me from swiping? I opened the Burp and started fuzzing the application and what is found is mentioned below.

During my analysis, it was observed that the number of like counts or “likeRemaining” given to the normal user is 50.
So, I started fuzzing and I found that the (/1/apitun/messages/send) POST request is used for sending messages to other users without validating the “LikesRemaining“count. It was also observed that when I sent a message without liking the profile it automatically liked that profile and it didn’t affect the “LikesRemaining” count which means you will LIKE any number of profiles with the normal user (Normal user = who doesn’t pay for it).

For exploiting this issue, I need “Userid”, so for this, I used a GET request (https://www.okcupid.com/match) to get the “userid”.
I made a script that automates the process of capturing the “userid” and sending a message to the users. This was shocking for me that within one day I liked 2000 plus user profiles which increased the probability of profile matching. In two days, I got the sixty-plus match.
“Automation Makes Your Life Easy”

Proof of concept:
Step 1: I logged into the application as “Rishu”. In this scenario, “Rishu” is an attacker. This is only for explanation purposes.
Step 2: In another browser, I logged in as “Victim”.

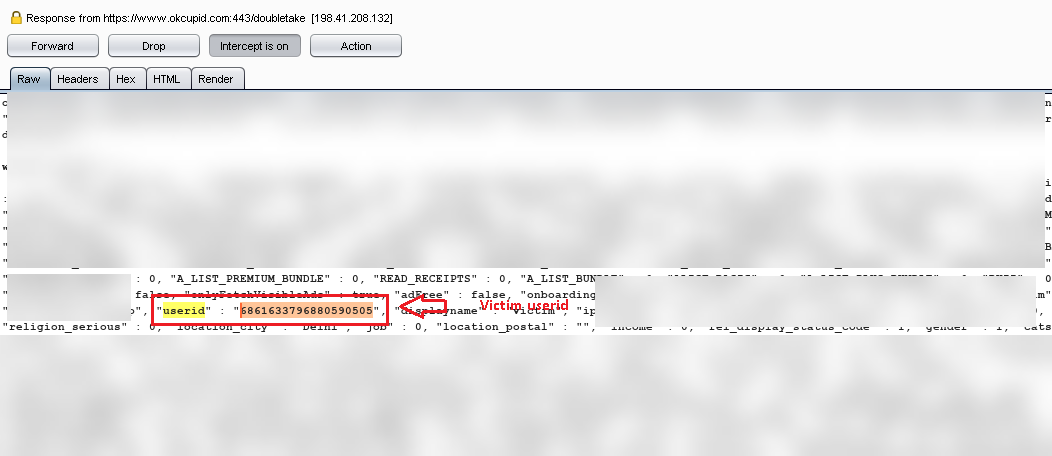
Step 3: I accessed the “Victim” profile from the “Rishu” account to get the “UserID” of the victim and capture the request and response in Burp (proxy tool).
The “userid” mentioned in POC was the “userid” of the victim that was accessed by an attacker.
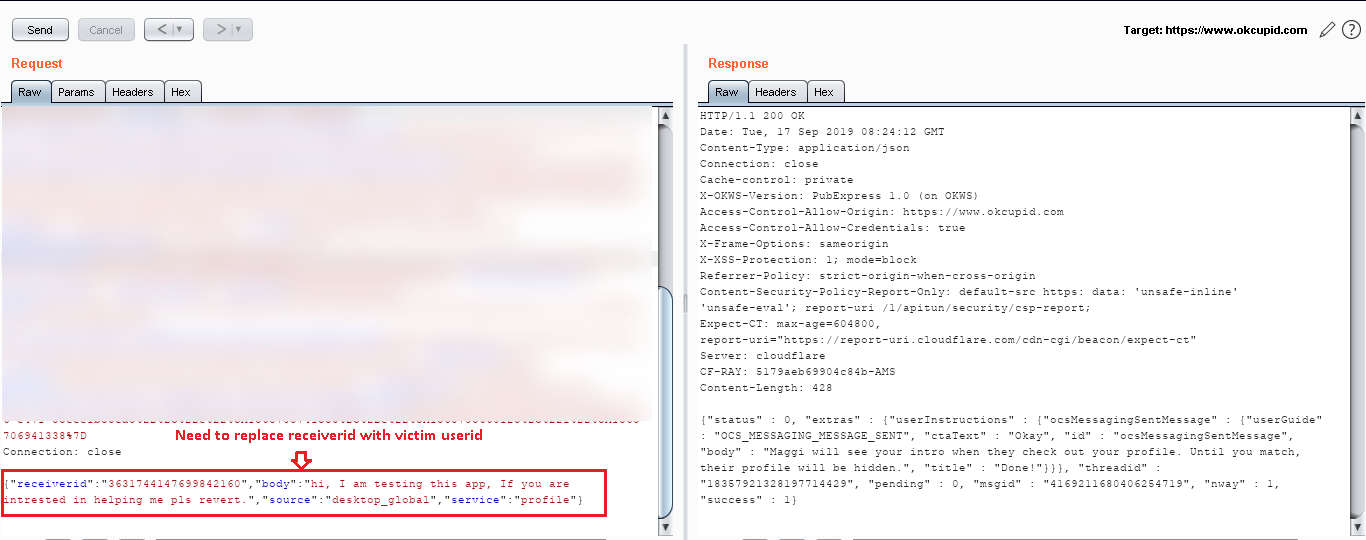
Step 4: Now I had the “userid” of the victim. I liked the random user to get the POST request of “message send” (/1/apitun/messages/send) and captured that request in Burp that I used later for attack and same used in the automatic script.
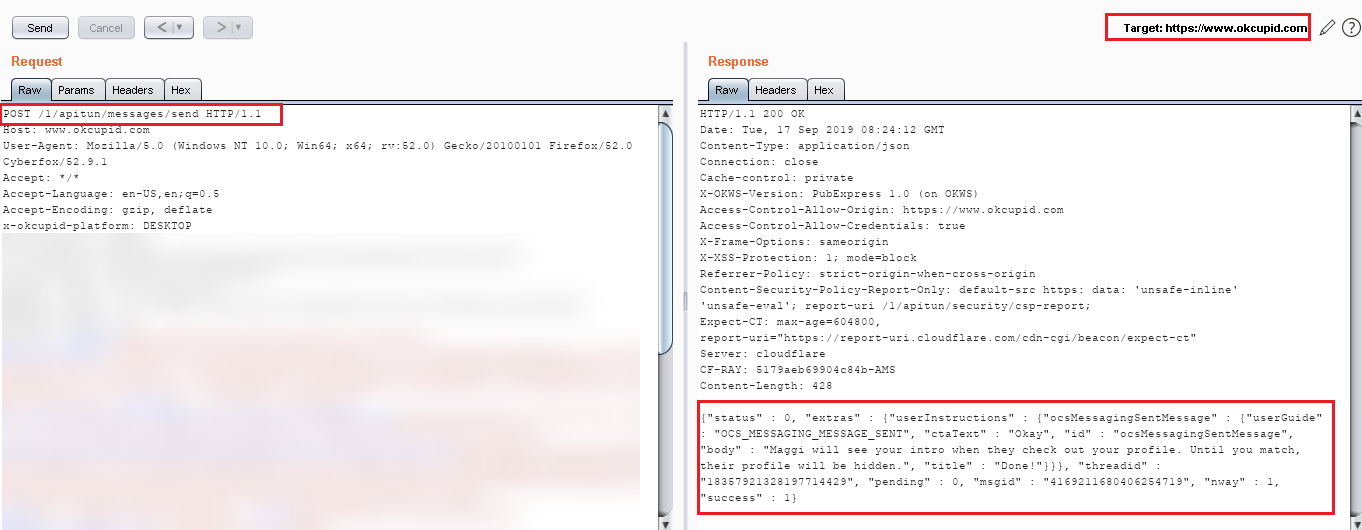
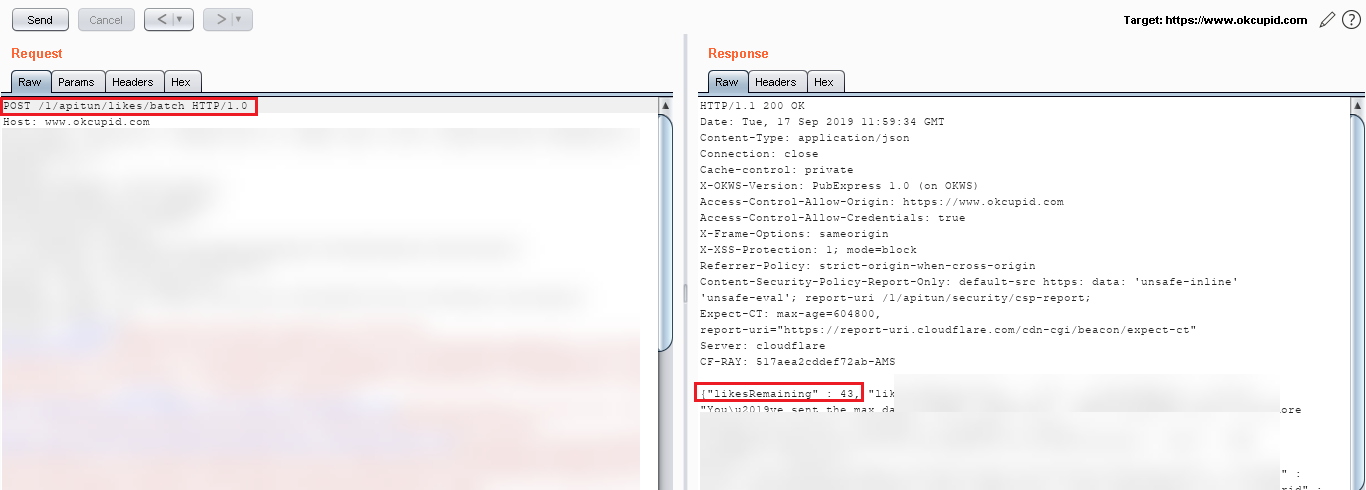
Step 5: Before sending the message to the victim, first I checked the “likeRemaining”count in my balance here it is 43.
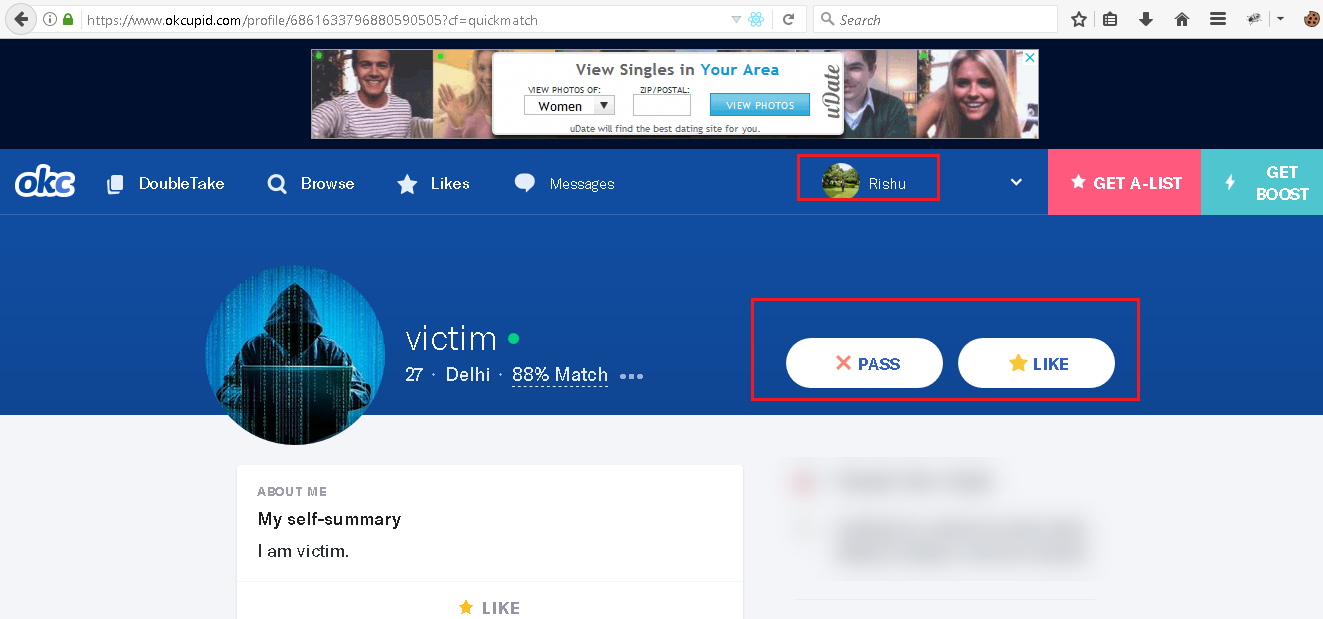
Step 6: Again, I checked the “Victim” profile from the “Rishu” profile to confirmed that the profile was not liked by “Rishu” an attacker. “Victim” profile is new so now like on his profile yet.
Step 7: Now I replaced the “userid” with “victim” userid in Step 4 request.
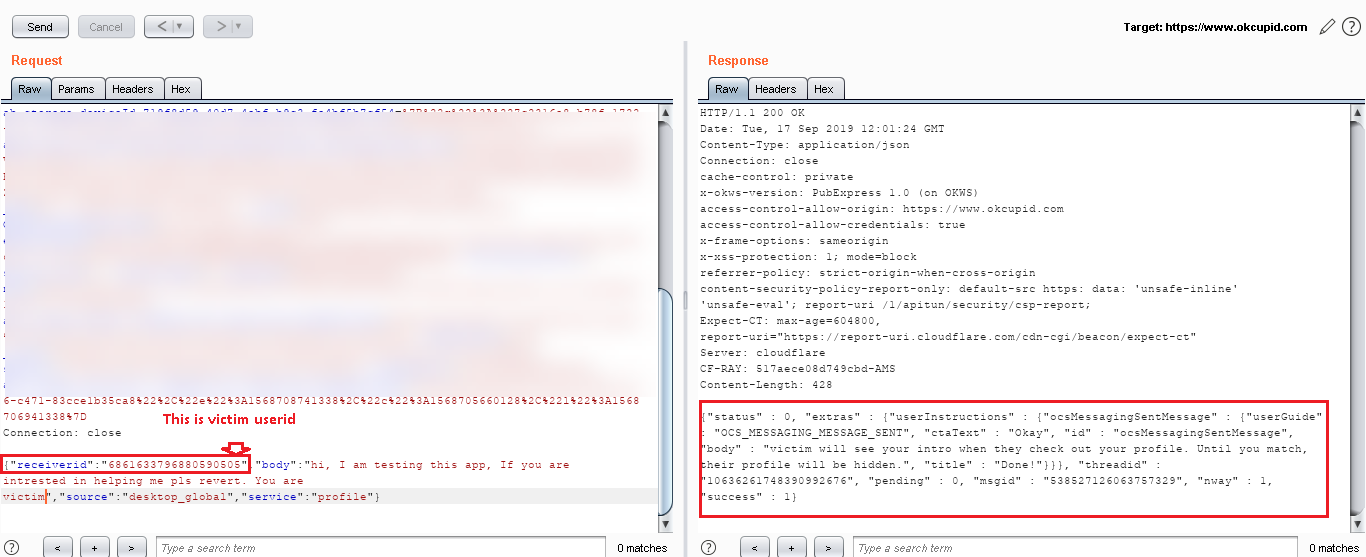
Step 8: After sending the above request the “LIKE” button changed to the “MESSAGE” button. This means that the victim profile successfully liked by an attacker i.e “Rishu”.

Step 9: Now again I checked the “LikesRemaing” count and it was same as above which was 43.
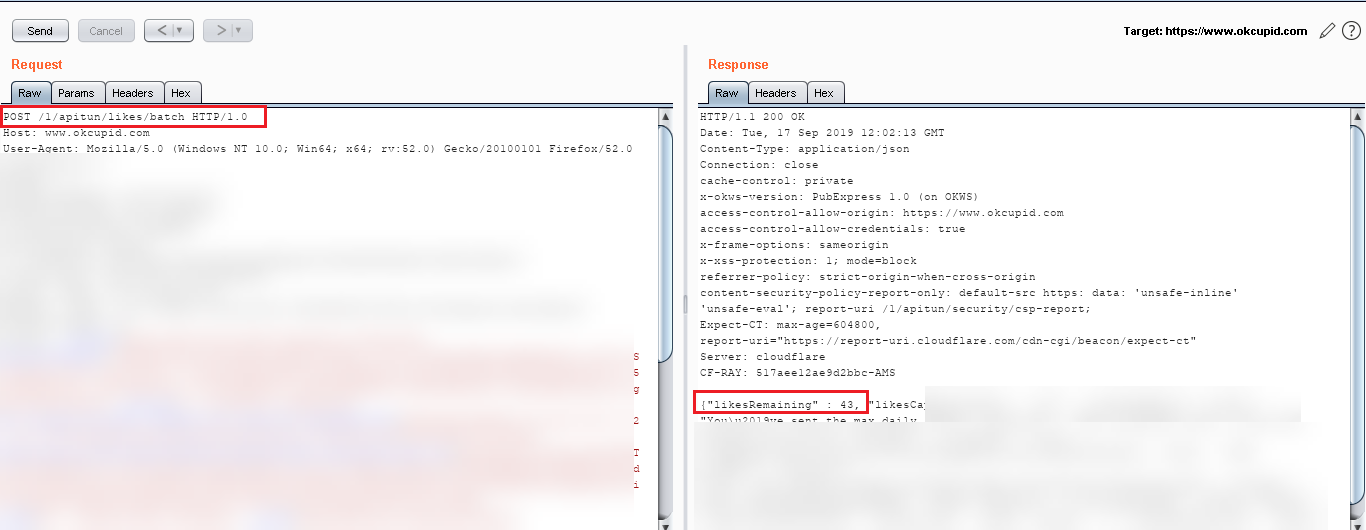
Step 10: Now, I again checked the “Victim” profile for the “LIKE” and it was observed that “Victim” successfully got the like. As “Victim” is also a normal user so not able to see the request.

Impact:
This vulnerability will impact the business and financial as this vulnerability allow a normal user to LIKE any number of users. This vulnerability will fail the business model of this application. This vulnerability allows the attacker to send the LIKE to all the users on this website that means it will increase the possibility of a profile match of the attacker. It causes financial loss as the attacker doesn’t want to buy for sending more like.
I made one Python script to automate this process which directly defines the impact of this vulnerability.
Exploit Code: https://github.com/crazywifi/OKCupid_LIKES_Restriction_Bypass
That “Somebody” is me who said this. :P
When I was writing this blog, I had already virtually dated 100 Plus in 3 days. It was a different experience to know and understand the different thought processes. This was my first experience on a dating site and I understand that this type of site helps you to understand the psychology and the thought process of others. It’s a different world of thought processes.
Being alone and actually sitting with our own thoughts can lead to such growth and realizations that are rare in our everyday busy lives.” — Kourtney Kardashian
Comments
Post a Comment